Communism: A theoretical economic system characterized by the collective ownership of property and by the organization of labor for the common advantage of all members. (Source.)
by Brian Shilhavy
Editor, Health Impact News
Big Tech Communism has arrived in the United States, as the U.S. has now surpassed China and other communist countries to become the world leader in spying on its citizens.
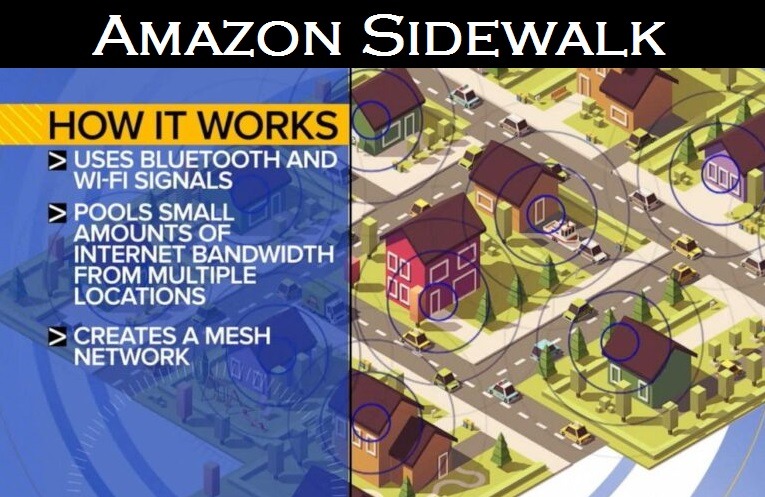
It was announced this past week that Amazon Sidewalk has now joined the Helium Network allowing all Internet of Things (IoT) devices, which are currently in the homes of almost all Americans, to be connected into one large mesh network nationwide.
The World Economic Forum’s (WEF) goals for the 4th Industrial Revolution and Great Reset where nobody will own anything and be confined into 15-minute “smart cities,” is clearly a modern day Big Tech version of communism, where the rights of the individual are sacrificed for the rights of the community.
This new system of surveillance, which is creating the ultimate police state, is well underway in the United States, which has, by far, the largest proportion of its population connected to the Internet, including cell phones, vehicles, cameras, and household appliances, than any other country in the world.
Amazon Sidewalk
Here is the description of the new Amazon Sidewalk mesh network that was just introduced this year, from the source, Amazon.com.
Everything you need to know about Amazon Sidewalk, the secure, low-cost network that can connect devices up to half a mile away
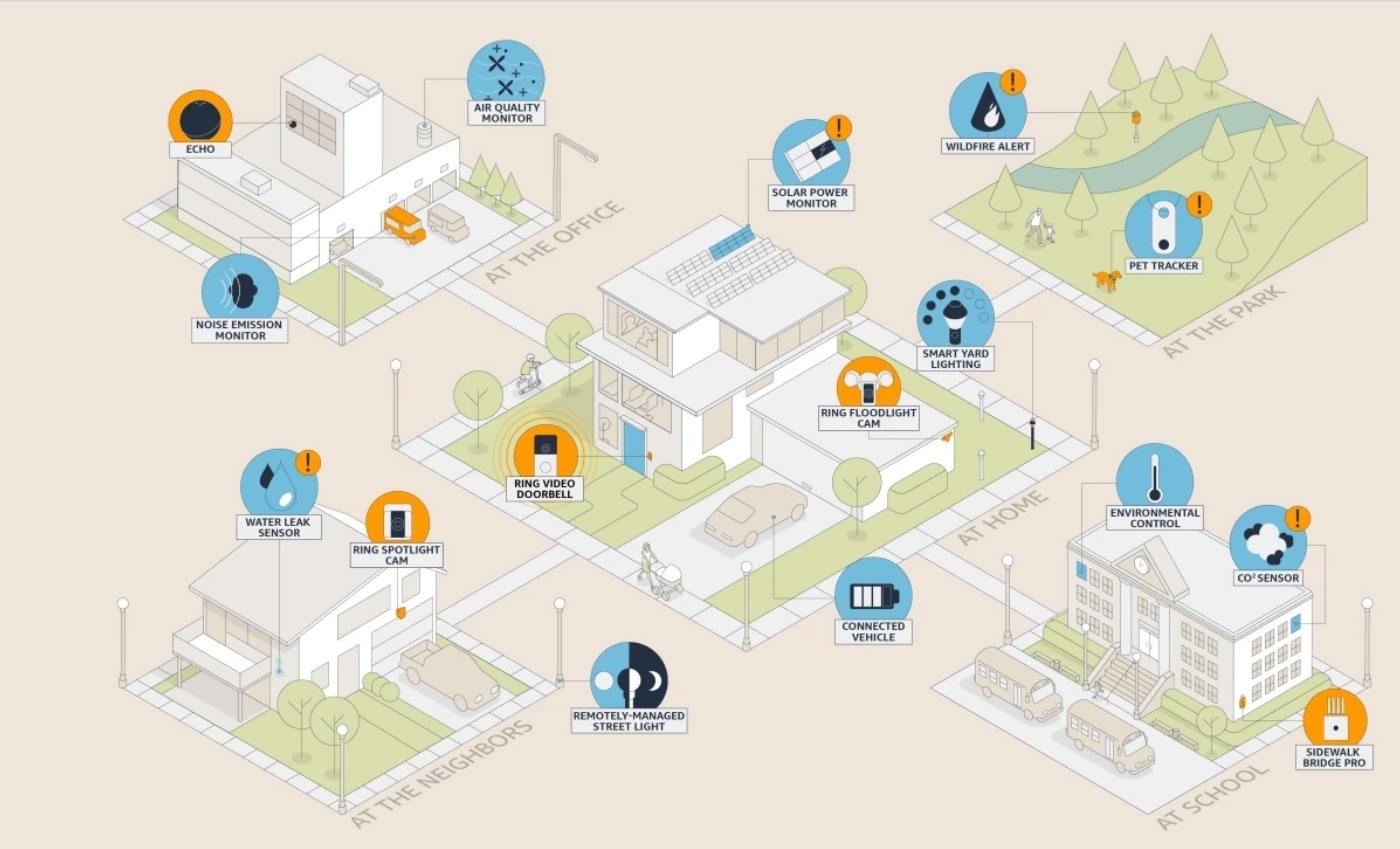
Imagine a network that securely connects your devices to the internet for free—from nearly anywhere. It exists. It’s called Amazon Sidewalk. And it has a range farther than Wi-Fi and is less expensive than the cost of a typical cellular network. This network opens the door to the creation of new types of devices for homes, businesses, and cities, which will help people intelligently track shipments, find lost pets, remotely detect smoke from wildfires, and so much more.
Amazon Sidewalk is a secure, free-to-connect community network designed to provide reliable connectivity for billions of devices. It’s already accessible to more than 90% of the U.S. population. (Source.)
Independent investigator Neil ‘Liberty’ Radimaker, writing for The Conscious Resistance Network, published an article this past week discussing the dangers this new network by Amazon presents.
Unveiling the Privacy Perils of Amazon Sidewalk
In a time where technology continues to shape our lives, the emergence of Amazon Sidewalk has ignited a fervent debate about the balance between convenience and privacy. As an independent investigator, I feel compelled to understand the deep complexities and potential dangers of this pervasive network.
This investigative report aims to shed light on the surveillance capabilities, coverage area, and the undisclosed collaborations surrounding Amazon Sidewalk.
In this report, we dive into the alarming dangers posed by these surveillance capabilities and the implications for personal privacy and autonomy.
Audio and Video Intrusion:
One of the most concerning aspects of Amazon Sidewalk is its ability to intrude into our private spaces without our explicit consent or knowledge. By silently capturing seamless audio and video data through devices like Ring cameras, Amazon Echo and other compatible smart home technologies. Sidewalk has the potential to turn every room of our homes into a watchful eye, constantly recording and analyzing our activities. This level of surveillance undermines the sanctity of our personal lives and raises questions about the boundaries of consent and individual autonomy.
Integration with Facial Recognition:
One of the most controversial aspects of Amazon Sidewalk’s privacy invasion potential is its integration with facial recognition technology. By combining video surveillance with facial recognition algorithms, Sidewalk will have the capacity to identify individuals and track their movements with alarming accuracy. Individuals can be identified and monitored, alerting officials when a person designated as “suspicious” is caught on camera.
Behavior Profiling:
By collecting a vast amount of data about our daily routines, habits, and preferences, Amazon Sidewalk has the potential to construct detailed profiles of individuals. Through sophisticated algorithms and data analysis, Sidewalk can track our movements, monitor our online activities, and even make inferences about our behaviors and interests. This level of profiling creates a comprehensive digital portrait, encroaching upon our autonomy and raising concerns about potential manipulation or discrimination.
Room Mapping and Blueprinting:
Amazon’s acquisition of iRobot, the maker of Roomba raises concerns about data sharing and collaboration with Amazon Sidewalk. The Roomba’s advanced features, including its mapping and blueprinting capabilities, introduce interesting privacy implications. With data collection and the ability to gather detailed information about our home layouts and furnishings. The Roomba can also silently record audio and video, analyzing our activities, intruding into our most private spaces.
Overlap of Coverage Reach:
Amazon Sidewalk’s extensive network coverage raises concerns about the widespread surveillance it enables. With a vast number of interconnected devices, this creates an overlapping network of surveillance that spans entire neighborhoods and public spaces. This level of coverage infringes upon our very sense of privacy, as our movements and activities can be captured and monitored from various angles and locations privately and publicly. Amazon Sidewalk’s ambition is to establish a nationwide network, the company currently claims it now provides coverage to over 90% of the U.S. population, including those who live in moderately rural areas.
Unregulated Data Collection:
The vast amount of data collected by Amazon Sidewalk raises significant concerns about its storage, usage, and potential for misuse. With access to intimate details of our lives, including our daily routines, social interactions, and even sensitive information, the potential for abuse or unauthorized access to this data is alarming. The lack of clear regulations and safeguards heightens the risks associated with such uncontrolled data collection.
This report by Radimaker does not even discuss the health hazards from frequency radiation by all these devices.
In my own residence, I do not have any Wifi turned on at all. I also own a simple EMF detector to see what levels of EMF radiation are coming into my residence from outside, as well as check if any appliances or devices in my residence are emitting frequencies.
I recently had someone visiting who wanted to use this device to see how much EMF pollution was coming from his cell phone. He tried turning on certain features of his cell phone, and the one thing that pushed my meter’s alarms to the highest level, was when he turned on his cell phone’s Bluetooth feature, which emits a 900 MHz WiFi-type signal.
Linda Kurtz at NoDirtyElectricity.com writes about how dangerous this is:
Amazon Sidewalk Irradiates You for Half a Mile
Amazon Sidewalk is the tech giant’s vision of smart neighborhoods connected by an array of Amazon gadgets. It’s a “mesh network,” similar to a smart meter mesh network. A mesh network means constant, nonstop wireless chattering.
Bluetooth makes it much worse. Amazon Sidewalk uses Bluetooth in addition to a 900 MHz WiFi-type signal.
What’s so bad about Bluetooth?
It has an erratically pulsing signal, full of constant highs and lows much worse than what you get even from smart meters and WiFi. The Bluetooth alone will extend several hundred feet.
How many neighbors do you have within a 300-foot radius of your home? You’ll be getting blasted by erratically pulsing Bluetooth from every home that has a device. (Full article.)
The Helium Network

Here is the Wikipedia entry on The Helium Network:
The Helium Network is a decentralized wireless Internet of Things (IoT) network using the LoRaWAN system, tied to the cryptocurrency Helium Network Token (symbol HNT).
Nodes on the network are generally owned and placed by individuals in their homes or offices, and they are rewarded for their participation in the network in payments of HNT.
The network aims to provide connectivity to IoT sensor devices in areas where wireless or mobile coverage is minimal, or requires too much power.
The Helium Network was begun by Helium, Inc. in 2013 as a network of LoRa gateway hotspots which could be deployed throughout an area by agreements with building owners, typically paid in conventional currency.
In 2017, the company’s funds were running low, so it switched to a new strategy: offering individuals payment in cryptocurrency to operate individually owned nodes in their homes or offices.
These individually owned nodes are purchased at costs of up to $500 each, and the payments to owners vary based on data usage but can be as low as $.10 a month. Hotspot operators would also have a vote in the operation of the network.
In 2022, Helium Inc. rebranded to Nova Labs Inc. and raised $200 million in a funding round led by Tiger Global Management and Andreessen Horowitz. (Source.)
Earlier this year (2023), it was reported that “mysterious antennas” were popping up in the foothills surrounding Utah’s Salt Lake City.
Salt Lake City officials are finding mysterious antennas across the foothills of the Salt Lake City metropolitan area. The first ones were discovered nearly a year ago, but more have been popping up in recent months. These devices appear to be relaying data across a wide area.
As first reported by KSLTV 5 in Utah, the mysterious devices consist of a battery box, a solar panel, and an antenna.
“These towers have been bolted into different peaks and summits and ridges around the foothills,” Tyler Fonarow, the city’s recreational trails manager, explained, “and it started with one or two, and now it might be as much as a dozen.”
Fonarow said whoever is installing these small fiberglass antennas doesn’t have a permit for authorization on public land. His department has been seizing the devices. They found one last week and plan to remove another later this month.
More antennas have been found on property managed by the Forest Service and the University of Utah.
Fonarow speculated the devices could be part of a decentralized wireless connectivity platform:
“It might be related to cryptocurrency and relaying networks and being able to make money off that,” he said, “so that’s another reason we want to stop it now before it becomes a dumping ground for dozens and dozens of more antennas.”
Some people who replied to the Facebook post speculated the devices could be part of the Helium network.
“Probably helium network like several have posted. Or some kind of mesh network repeaters? I don’t understand why they are being torn down and huge effort to take them off public lands, when if it is a mesh network repeater, can be used by the public, and is very important in emergency/communication failure situations,” one person said.
“Those are very clearly off-grid Helium miners,” another person said.
If the speculation is correct, these mysterious antennas could be hotspots connecting to a wireless blockchain-based network for Helium. This entirely new incentive model allows people to set up hotspots that act as Helium miners and serve data to devices. People can earn money by simply buying a hotspot and plugging it in. (Full article.)
The Helium website claims that they now have 991,170 total hot spots.
Last week it was announced that The Helium Foundation has partnered with Oxit to create Oxtech Module, a product to connect Internet of Things (IoT) devices to both the decentralized wireless network, Helium, and Amazon Sidewalk. (Source.)
Helium mobile is currently in beta, and once it is launched it will be available on everyone’s cell phone which will greatly increase its coverage.
Tips on Opting Out of the New Big Tech Communist Network
The best thing you can do to avoid being watched by Big Tech is to just stop using their products, especially a cell phone.
Since I know this is too difficult for most people, here are some good articles giving tips on how to reduce your exposure to Big Tech’s monitoring of you.
How to stop your smart devices from listening to you and recording what you say
BY KIM KOMANDO
KOMANDO.COM
Excerpts:
Voice recognition is undeniable proof that we live in the future, making daily life more convenient. But what’s the downside for always-on devices that constantly listen for commands?
It’s just that: They’re always listening. Nearly all voice-activated technology uses microphones that listen for “wake words.” It also means companies like Apple, Facebook and Google hear all your commands and can pick up conversations if your device thinks it hears the wake word. And these devices are accidentally activated far more often than you might feel.
We don’t blame you if you’re uncomfortable with how much your smart devices can hear in your home. Your smartphone alone contains cameras, a microphone and many other tools that can be misused against you. If you want to take control of your privacy and keep conversations “behind closed doors,” here’s how to stop your smart devices from listening.
Blocking stalkerware
A common way your devices can spy on you has nothing to do with the companies who made them. Instead, this method involves tampering with your tech so it can spy on what you do and say. It’s called “stalkerware,” and if one of these dangerous apps is installed on your computer or smartphone, the person behind it may already know quite a bit about you.
Stalkerware apps are often marketed for “parental control” purposes, but these apps can be abused in the wrong hands.
They generally collect your web browsing history, text messages and phone calls. Some can even capture what you’re doing on-screen. So how can you spot them? A surge in data usage, odd charges on your bill and other red flags are clues that something is wrong. Tap or click to see the top 6 signs and what you can do.
Foiling Facebook
Facebook sometimes requests access to the microphone for video chatting and text-to-speech purposes. But if you’re uncomfortable giving Facebook control of your mic, here’s how to stop it.
(Note: There are many Android manufacturers, so the steps outlined in this article may differ from your model. If so, check with your model’s manual.) Don’t have your manual handy? Tap or click here for thousands of free online user manuals.
For iPhone
- Open the Settings app. Then, scroll down and tap Facebook.
- Toggle the green switch next to Microphone to the off position.
Another way is:
- Open the Settings app. Then, scroll down and tap Privacy & Security.
- Locate the menu labeled Microphone and tap it.
- Find Facebook in the list of apps and toggle the Green switch to the off position.
For Android
- Open the Settings app. Then, scroll down and tap Personal.
- Tap Privacy and safety, followed by App Permissions.
- Tap Microphone and locate Facebook.
- Toggle the slider to the off position.
If you shoot a video or chat with a friend, return to these settings and enable your mic. Switch it off again when you’re finished.
Your smart TV
Many smart TVs come equipped with voice recognition. Unfortunately, this means they, too, can listen in. Worse still, some popular smart TVs spy on your viewing habits and sell that data.
If you want to stop your smart TV from listening to you and scanning your channel-surfing history, check out our detailed guide to disabling these features on TVs made by Samsung, VIZIO, LG and more.
Tap or click here to see the easiest ways to stop your smart TV from tracking you.
Untangling ultrasonic technology
Are you familiar with ultrasonic tech? Most people aren’t, but your smart devices are aware of it. “Ultrasonic” refers to radio waves that humans can’t hear. They’re perfect for stealthily issuing commands to smart devices.
Why would anyone want to collect these inaudible sounds? It comes down to money. Apps that use ultrasonic tech are constantly looking for “beacons,” which are audio clues that suggest where you shop and what you like to buy. These apps then pair browser cookies to your device to track you.
Thankfully, in 2017, Google announced that 234 Android apps using ultrasonic tracking would be banned or suspended. In 2021, the company banned cross-platform tracking as part of its ad policy.
But if you’re still unsure whether an Android or iOS app uses ultrasonic tech for other reasons, you can always disable the microphone using the exact steps you used for Facebook.
For iOS
- Open the Settings app. Then, scroll down and tap Privacy & Security.
- Locate the menu labeled Microphone and tap it.
- Find the app you want to turn the mic off for in the list of apps and toggle the green switch to the off position.
For Android
- Open the Settings app. Then, scroll down and tap Personal.
- Tap Privacy and safety, followed by App Permissions.
- Tap Microphone and locate the app you want to turn the mic off for.
- Toggle the slider to the off position.
With your devices no longer listening, you can relax and feel less paranoid about using your tech. And the best part: You can always turn the microphones back on again if you want to use them. Just make sure you’re careful about what you say when they’re on — and don’t forget to turn them off when you’re finished.
You may also like: 30-second privacy check every Google and Facebook user must do today.
Read the full article at KOMANDO.COM
Is Someone Spying On Your Cell Phone? 10 Ways To Tell & How To Stop Them
Do you feel like someone is watching you, monitoring or listening in on your phone calls? In this article, I’ll explain how to tell if someone is spying on your smartphone and what to do about it.
Excerpts:
Your smartphone stores a great deal of personal information. Let’s face it, your whole life is on that thing. You use your cell phone on a daily basis, sending emails and text messages, making calls, listening to voicemail messages, taking and sharing videos and photos, using social media, and so much more.
What if someone was able to access all of that personal data? That could be a disaster.
Here are the 10 ways to tell whether or not someone is monitoring your smartphone.
1) Unusually High Data Usage
Has your monthly data usage spiked recently? Is your device suddenly using more data than normal, bumping up against your monthly data allotment, yet you haven’t changed your online habits? That could indicate that someone has installed spyware on your device.
Lower-quality spy tools will try to send as much data about your device back to their home base (AKA the bad guys) as they possibly can. This can use large amounts of data.
On the other end of the spectrum, some of the spyware makers are quite skilled at it, and their sneaky apps are much more selective with what info they look for and send back home. This makes detection a bit tougher.
It all comes down to making sure that you stay aware of your monthly data usage and pay close attention to any sudden spikes in usage that you might see.
While you can contact your wireless carrier to check on how much data you’ve used, you can also check on your device. This means you can quickly check data usage without the need to search around on your provider’s website or app for data usage information.
How to Check Cellular Data Usage on Android
To check your cellular data usage on an Android 10 device, do the following. (The process should be similar on other versions of Android.):
- Open the Android Settings app.
- Tap “Mobile Network” (It’s in the “Network & Internet” section.)
- On the Mobile Network screen, tap “App Data Usage.”
- Here, you can view your current cellular app data usage. (You can select other date ranges for viewing.)
![]()
How to Check Cellular Data Usage on an iPhone
To check your cellular data usage on an iPhone running iOS 16, do the following. (The process should be similar on other versions of iOS and on iPads running iPadOS.):
- Open the iOS 16 Settings app.
- Tap the “Cellular” menu option.
- In the Cellular menu, tap the “Usage” menu option.
- On the Usage screen, you can view the data usage for the current month.
![]()
2) Cell Phone Shows Signs of Activity in Standby Mode
While you should expect your iPhone or Android phone screen to light up when you receive an incoming call, message, or most other types of notifications, your smartphone’s screen shouldn’t be lighting up for no reason while it’s in standby mode.
If you see your device’s screen light up, hear unexpected noises or sounds, and then you don’t see any new notifications on the screen, something could be up.
3) Unexpected Reboots
Is your smartphone rebooting for no obvious reason or without you manually rebooting it? Someone may have unauthorized remote access to your smartphone.
Unexpected reboots may indicate someone has remote admin access and can reboot your device at will. This would also indicate they have all sorts of other access to your device and the personal data stored on it.
It could also mean the latest app or operating system you recently downloaded has a bug in it. Check for new updates for the device’s OS or for the app. See if you can duplicate the device reboot by using the app that was open when it happened.
On your Android device, you can install and run antivirus or anti-malware security software to scan your device. iOS users will find that antivirus scanners are not available, and in the sandboxed iOS operating system, it’s more likely that there is a bug in an app or in the OS that is causing the reboots.
4) Odd Sounds During Calls
In the days of analog cell phone networks, weird noises in the background and unstable connections were to be expected. However, today’s all-digital cell networks usually provide connections that are stable and mostly noise-free.
So, if you are hearing weird noises in the background, or (even worse) hear a voice that doesn’t belong to the person you called, there is a possibility that someone is monitoring or recording your conversation.
5) Unexpected Text Messages
Have you either received unexpected messages with weird characters in them or have your friends or other parties reported receiving weird or offensive messages from your phone?
This can be a sign that you have spyware or malware installed on your smartphone. SMS worms spread themselves through the online world by sending text messages with links embedded in them. If the victim taps the link, the worm can infect their smartphone.
On your Android device, you can install and run security software such as antivirus or anti-malware to scan your device. iOS users will likely not have to worry about these types of worms, as they target Android devices for the most part.
Also, be wary of clicking links in these text messages, as such links can also be used to scam you via phishing schemes to steal your personal and/or business information. This is true on both the Android and iOS device platforms.
6) Deteriorating Battery Life
If you see your device’s battery life begin deteriorating rapidly and unexpectedly, that could mean your battery is old and in need of a replacement. Or, it could mean that your device is infected with spyware, and the additional load it’s putting on your smartphone is draining the battery quicker than usual.
Spyware monitors all of your on-device activities and sends information about these activities back to the bad actors that infected your device. Shortened battery life often goes hand-in-hand with increased data usage due to the activities of the spyware.
Taking screenshots, copying and pasting text, recording your conversations, and possibly taking photos or recording video can eat up battery life at an alarming rate. This is especially obvious when your smartphone is supposedly idle.
If you’re not sure whether it’s just an old battery or actual spy software, test this by trying a different set of batteries or checking your device’s battery in a different device. Then, monitor the battery usage.
Sorry iPhone users, your device’s batteries are not removable. But, you can make a Genius Bar appointment and they can check your battery for you. Users running iOS 14 and up can take advantage of a privacy feature that alerts you when an app on your device is using its camera or microphone.
If an app is using your iPhone’s camera, you’ll see an indicator light up at the top of your device’s screen, as shown here:
![]()
If an app is using your iPhone’s built-in microphone, you’ll see an indicator light up at the top of your device’s screen, as shown here:
![]()
While it is perfectly normal to see either of these indicators light up when apps are using either the camera or the mic, seeing them light up when you’re not actively recording video or audio should serve as a warning sign that something might be up.
Determining Which Apps Have Access to Your Device’s Microphone or Camera
It’s easy to check your device to find out which apps currently have access to your device’s microphone or camera.
On the iPhone, do the following:
- Open the Settings app.
- Tap “Privacy” (“Privacy & Security” in iOS 16) in the Settings app.
- Tap either “Microphone” or “Camera” in the privacy menu.
- On the next page, you can view which apps have access to the selected feature. You can also toggle the access on or off in this menu.
![]()
On an Android Device, do the following:
These instructions are for generic Android 10. The steps will be similar for customized versions of Android 10 or for other versions of Android. Check with your device’s manufacturer for more information.
- Go to the Settings app.
- Tap “Privacy.”
- Tap “Permission Manager.”
- Tap “Camera” or “Microphone.”
- Here, you can view which apps have access to the selected feature. You can also tap each app to turn the access on or off.
![]()
7) Increasing Battery Temperature in Idle Mode
While increased battery temperature can be a sign of multiple technical issues, it can also indicate that unauthorized activities, like spyware activities, are occurring in the background.
If you haven’t used your smartphone recently, and it’s just been sitting idle on your desk, it shouldn’t be warm or hot to the touch. If it is overly warm, then spyware could be working behind the scenes, collecting information, and sending it back to the bad actors’ home base.
8) Increased Device Shut Down Time
Your smartphone, much like a Mac or Windows PC, attempts to shut down all active processes before turning itself off or when it is rebooted.
And, much like your computer, occasionally those processes can hang up and either prevent or greatly slow the shutdown process. While this can happen to any device, you may notice that it is happening more often than usual if your device has been infected with spyware.
You may notice that your smartphone takes longer than usual to shut down right after you’ve finished an active period with your mobile phone. This could mean the spyware is working in the background, saving its ill-gotten information and sending it back to home base.
9) Difficulty in Shutting Down or Rebooting Your Device
In addition to slowing the shutdown process of your smartphone, spyware can also prevent your device from shutting down or rebooting completely.
Again, this can be caused by a harmless app misbehaving, but if it just started happening recently, or is happening more often than not, your device might be infected with spyware. (Did anyone else hear Jeff Foxworthy say that last sentence in their head? Just me? Okay.)
10) Your Cell Phone is Growing Increasingly Slower
High-end smartphones made in the last five years or so should run fast and not show many performance issues during day-to-day use. If you notice your smartphone is lagging, performing much worse than usual, or is suddenly running out of resources like memory or storage space, it might be infected with spyware.
This is tougher to tell with older smartphones or low-priced budget handsets like you get off the rack at Walgreens. But, if you pay attention to how your smartphone usually performs, you can usually tell if something is going on.
Read the full article at Pixelprivacy.com.
Comment on this article at HealthImpactNews.com.
This article was written by Human Superior Intelligence (HSI)
See Also:
Understand the Times We are Currently Living Through
New FREE eBook! Restoring the Foundation of New Testament Faith in Jesus Christ – by Brian Shilhavy
Who are God’s “Chosen People”?
KABBALAH: The Anti-Christ Religion of Satan that Controls the World Today
Christian Teaching on Sex and Marriage vs. The Actual Biblical Teaching
Exposing the Christian Zionism Cult
The Bewitching of America with the Evil Eye and the Mark of the Beast
Jesus Christ’s Opposition to the Jewish State: Lessons for Today
Identifying the Luciferian Globalists Implementing the New World Order – Who are the “Jews”?
The Brain Myth: Your Intellect and Thoughts Originate in Your Heart, Not Your Brain
What is the Condition of Your Heart? The Superiority of the Human Heart over the Human Brain
The Seal and Mark of God is Far More Important than the “Mark of the Beast” – Are You Prepared for What’s Coming?
The Satanic Roots to Modern Medicine – The Image of the Beast?
Medicine: Idolatry in the Twenty First Century – 10-Year-Old Article More Relevant Today than the Day it was Written
Having problems receiving our emails? See:
How to Beat Internet Censorship and Create Your Own Newsfeed
We Are Now on Telegram. Video channels at Bitchute, and Odysee.
If our website is seized and shut down, find us on Telegram, as well as Bitchute and Odysee for further instructions about where to find us.
If you use the TOR Onion browser, here are the links and corresponding URLs to use in the TOR browser to find us on the Dark Web: Health Impact News, Vaccine Impact, Medical Kidnap, Created4Health, CoconutOil.com.